Secure Clustering Centralized Management
Centralized out-of-band management for IT infrastructure provides access and visibility during critical failures
Large enterprises, service providers, and data centers could have hundreds of console servers connected to thousands of servers, switches, and routers across multiple sites. To simplify management and respond more swiftly to issues, network administrators require access to all console ports via a single portal view from any web-enabled device. Perle's built-in Clustering Software centralizes all your network and IT infrastructure into a single application and provides secure reliable access and visibility during normal operations and critical network failures. Scalable to suit any business requirement, Clustering Centralized Management reduces human error and guarantees repeatability.
- No annual licences fees. No additional hardware required
- This central network hub and management portal for Perle IOLAN Terminal Servers provide a resilient management resource
- Scalable administration from provisioning to routine operations and disaster recovery
- Seamless, always-available connectivity, over LAN or remotely over WAN
- Centralized, secure, end-to-end out-of-band management
- Access managed devices by name, regardless of how they are connected
- Purpose-built to give 24/7 console access to any device during network meltdowns
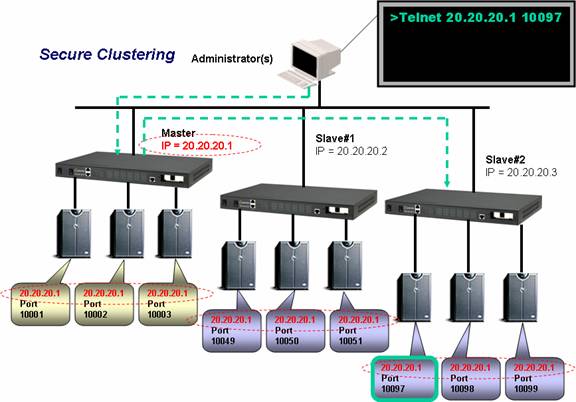
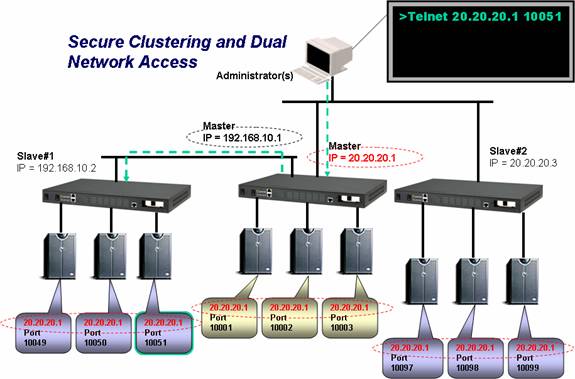
By defining a master IOLAN Console Server (or for resiliency a second one), multiple slave IOLANs can be configured to form a single secure Console Server cluster. This presents a complete view of all ports associated across Master and slave units. There is no need to remember what is the IP address of the console server that is associated with the target console port. This saves the administrator valuable time to expedite problem resolution. Access to the IOLAN cluster view can be accomplished through the IOLAN’s EasyPort Web with an internet browser or CLI based EasyPort though a Telnet or SSH application. The easy-to-use interface enables users to quickly segment the nodes on their network regardless of size. Simple role-based permissions and node association ensures the right access levels to all users.